Some privacy professionals consider controls frameworks to be ‘their secret sauce’, but I think of them as ‘our secret sauce’ as an industry. I feel we should all share knowledge and should learn more ourselves through that sharing. This article is not meant as a ‘how to’ but rather a ‘did you know’ and ‘look over here’ guide. I hope it brings you some new knowledge, enhances old knowledge, or even makes you think: ‘hey, I knew that already, but I like how it is synthesised here’.
In the previous article in the series, we discussed the CIA triad as it applies to privacy, not just cybersecurity. We also discussed important definitions of cybersecurity and data protection terms. After having established the fundamentals in that article, in this second of three articles, we are going to outline how we, in the privacy community, can use control frameworks from the standards bodies NIST and ISO.
Frameworks are hugely important in both cybersecurity and privacy. I am presenting two frameworks here (albeit one is technically a standard) from NIST and ISO. There are several others, such as CIS controls, HITRUST Common Security Framework, and COBIT. I chose NIST and ISO for two reasons: I know them well, and they provide meaty detail to the required privacy controls rather than generic statements such as ‘having appropriate policies in place’. (For the record, such statements of controls drives me insane, because ‘appropriate’ is such a subjective word).
What’s the difference between standards and frameworks?
On a point of technicality and the use of the terms ‘standards’ and ‘frameworks’: ISO produces standards, where NIST produces frameworks. What is the difference? Standards (according to the dictionary) are set up/established by an authority as a rule for the measure of quantity, weight, extent, value, or quality. Their single most import characteristic is their rigidity. That is, a product is either fire retardant or it isn’t. Frameworks, on the other hand (according to the dictionary) are structures intended to serve as a support or guide for the building of something that expands the structure into something useful. However, in our industry we often rely on ‘standards’ as frameworks. In other words, we don’t want to attest or certify to the standard but we want to use the standard to guide us in a flexible way. So when I refer to ISO standards as frameworks in this blog, my intention is to explain that you don’t need to use it rigidly in this case – you can simply refer to it as a controls framework.
We can use these frameworks to determine mitigating controls you can apply to each component in the CIA triad, together with the preventative/detective controls that can reduce the risk. You can use these controls to help you complete Records of Processing Activity (ROPAs) and Data Protection Impact Assessments (DPIAs), particularly the more complex technical ones.
Which framework to use and when? The NIST frameworks for privacy and for cybersecurity
I use the ISO27001 framework – and its supplemental guidelines ISO27002 – in a work context as it is the tool of choice in BH Consulting. It also provides a risk-based approach which ties nicely with GDPR’s risk-based approach. I use NIST frameworks for any authorship and research I am undertaking, as NIST is open access and therefore available to the public to use without subscription. NIST is also my go-to for cybersecurity and privacy definitions in the US context.
The NIST frameworks for privacy and for cybersecurity
NIST frameworks are produced by the cream of subject matter experts (SMEs) in industry, together with a collaborative committee that develops and tests them. NIST has a framework for cybersecurity and for privacy. Both frameworks present a risk-based approach to managing risk in their respective area, and each framework is presented in three parts: the Core, the Implementation Tiers, and the Profiles.
The Framework Core is a set of activities (cybersecurity/privacy depending on which framework), desired outcomes, and applicable references that are common across organisational sectors. The Core presents industry standards, guidelines, and practices in a manner that allows for communication of activities and outcomes across the organisation from the executive level to the implementation/operations level. The Framework Core consists of several Categories and Subcategories – which represent discrete outcomes for activities, together with matching references to existing standards, guidelines, and practices for each subcategory.
Privacy and cybersecurity in a single framework
Combining both the privacy framework and the cybersecurity framework into one tool was only a matter of time and, in early 2023, NIST ‘magicked’ them together to form the Cybersecurity and Privacy Reference Tool (CPRT). The concept underpinning this tool was that its development was to be the first of three phases of tool enhancement. Phase I was called ‘freeing the data’, i.e. converting the frameworks and their guidelines (which were in publication format) into interactive drill-down tools connected to a database of controls and risks. You can download the tool, but you need to use the online version if you want to avail of the interactive element with drilldowns.
This tool shows you what has been adapted from the cybersecurity framework, what is identical to the cybersecurity framework and what is not sourced at all from the cybersecurity framework. It is presented in five categories:
- IDENTIFY: Develop the organisational understanding to manage privacy risk for individuals arising from data processing.
- GOVERN: Develop and implement the organisational governance structure to enable an ongoing understanding of the organisation’s risk management priorities that are informed by privacy risk.
- CONTROL: Develop and implement appropriate activities to enable organisations or individuals to manage data with sufficient granularity to manage privacy risks.
- COMMUNICATE: Develop and implement appropriate activities to enable organisations and individuals to have a reliable understanding and engage in a dialogue about how data are processed and associated privacy risks.
- PROTECT: Develop and implement appropriate data processing safeguards.
If you are interested in ‘controls’, you will find the meat in the drilldowns on the CONTROL section and the drilldowns on the PROTECT section. However, if you like to go straight to the publications on controls, then I can direct you to another part of the tool which is here. This link presents each of the different publications that the tool has glued together. Note the link to ‘Security and Privacy Controls for Information Systems and Organisations’: This brings sets of controls together so you can more readily conduct a ROPA or DPIA
| Reference Data Set | Publication Title | Status |
|---|---|---|
| SP 800-221A | Technology and Risk Outcomes, Draft | Draft |
| SSDF | Secure Software Development Framework (SSDF): Recommendations For Mitigating the Risk of Software Vulnerabilities | Final |
| NISTR 8259B | IoT Non Technical Supporting Capability Core Baseline | Final |
| SP 800-Rev 5 | Security and Privacy Controls for Information Systems and Organisations. 5.1.0 | Final |
| NISTR 8259A | IoT Non Technical Supporting Capability Core Baseline | Final |
| SP 800-171 Rev 2 | Protecting Controlled and Unclassified Information in Nonfederal Systems and Organisations, Revision 2 | Final |
| Privacy Framework | NIST Privacy Framework: A Tool for Improving Privacy Through Enterprise Risk Management, Version 1.0 | Final |
| Cybersecurity Framework v1.1 | Framework For Improving Critical Infrastructure Cybersecurity, Version 1 | Final |
| SP 800-171 Rev 1 | Protecting Controlled and Unclassified Information in Nonfederal Systems and Organisations, Revision 1 | Withdrawn |
| SP 800-53 Rev 4 | Security and Privacy Controls for Information Systems and Organisations, 4.0.0 | Withdrawn |
Using ISO 27001 and ISO 27701
[Editor’s note: these standards should be referred to as ISO/IEC, but for brevity I’ll refer to them simply as ISO].
ISO creates standards in a similar collaborative manner to NIST. National bodies consult their local SMEs and feed that back to ISO’s Technical Committee (TCs). TCs are made up of professionals from industries, government bodies, and invited experts.
ISO 27001 is part of a set of standards developed to handle information security: the ISO 27000 series. Its full name is ‘ISO/IEC 27001 – Information security, cybersecurity and privacy protection — Information security management systems — Requirements’. The term Information Security Management System is most often referred to as the ISMS. ISO 27002 is a supplement to the series that focuses on the information security controls that are listed in Annex A of ISO 27001. However, where Annex A outlines each control in a sentence, ISO 27002 provides detailed implementation guidance of up to one page per control.
In 2022, ISO released an updated version of the ISO 27001 standard to take into account modern business and technical needs and to align more closely with NIST. Annex A originally contained 114 controls, divided over 14 chapters, whereas the 2022 version now contains 93 controls, divided over four chapters:
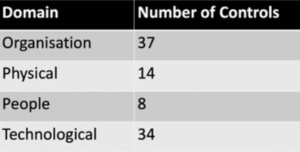
Also added were a set of attributes, which are broken down as follows:
| Reference Data Set | Information & Security Principles | Cyber Security & Concepts | Operational Capabilities | Security Domains |
|---|---|---|---|---|
|
|
|
|
|
The Privacy Extension to ISO 27001
In 2019, ISO 27701 was built to complement ISO 27001:2013, and is often referred to as the privacy extension of ISO 27001. The ISO 27701 standard is currently being revised to align with the new 2022 version of ISO 27001. Instead of an having an ISMS (as per ISO 27001), ISO 27701 specifies requirements and guidance for a Privacy Information Management System (PIMS). This creates a strong integration point for aligning security and privacy controls. ISO/IEC 27701 accomplishes this integration through a framework for managing personal data that both data controllers and data processors can use. The graphic below outlines a list of the clauses in ISO 27001 that ISO 27701 extends to provide not only security but also privacy and data protection requirements and controls.
| ISO 27001 Clause | Publication Title |
|---|---|
| 5.1 | Top Level Commitment for Privacy Policy and PIMS integration including: |
| 5.2 | 1. Resourcing/ Establishment of Roles |
| 5.3 | 2. Communication (Internal/External) |
| 7.1 | 3. Anticipated Outcome
4. Control and Guidance |
| 7.4 | 5. Continued Improvement of PIMS |
| 6.2 | PIMS/Privacy Objectives |
| 7.2 | Competency profiles of individuals assigned to privacy roles |
| 7.3 | Awareness of the PIMS policy and how personnel contribute to the establishment and improvement of the system |
| 7.5 | Documentation for PIMS with additional considerations on information and documentation of non-organic to the organisation |
| 8.1 | PIMS Risk Treatment Activation |
| 8.2 | PIMS Risk Assessment Process |
| 8.3 | PIMS Risk Treatment Plan including amendments to existing risk registers |
| 9.1 | PIMS Performance and analysis of PIMS effectiveness including: |
| 9.2 | 1. Internal Audit |
| 9.3 | 2. Management Review |
| 10 | PIMS Continuous Improvement considerations |
ISO standards are not free and there is a fee for each standard – but they are incredibly detailed. However, if you search the internet for a ‘list of controls in Annex A of ISO 27001’ and ‘list of controls in ISO 27002’. Although that won’t give you the whole standard, you will find lots of free material that may help you complete your ROPA or DPIA.
In the next and final blog in the series, I will present a checklist of items that privacy professionals can use to assess security controls.
Dr Valerie Lyons is the Chief Operating Officer of BH Consulting.


